How to find Multiple Vulnerabilities in Symfony profiler (debug mode)
Hi Friends!!!
This is Rahad Chowdhury. I am a Cyber Security Researcher from Bangladesh.
Today’s topic is all about Symfony Web Framework Profiler and Debug Mode enabled bug, which find multiple vulnerabilities.
What is Symfony Profiler?
Symfony Profiler is powerful development tool that gives detailed information about the execution of any request.
What is the Symfony Profiler vulnerability?
Exposing debug features in a production enviroment often leads to server vulnerabilities. The Symfony web profiler component exposes very sensitive information and provides dangerous features that can be abused by attackers to retrieve application files.
How to get multiple vulnerabilities?
I have a target domain that example.com (use your domain).
Now open your browser and visit example.com domain.
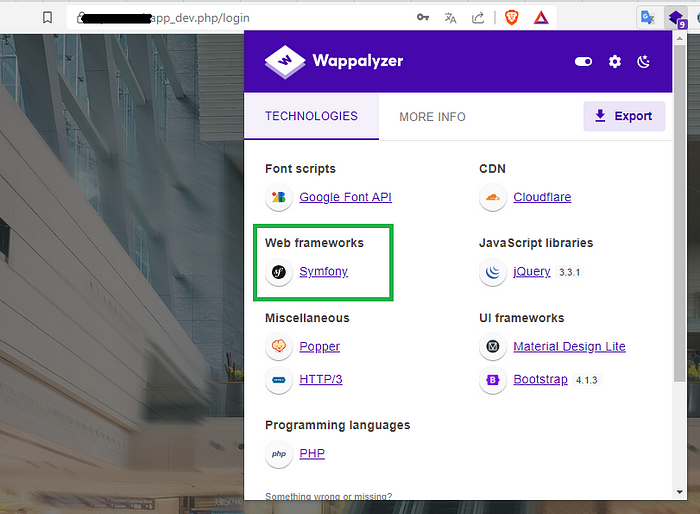
Then Install wappalyzer extension/addon in your browser (Wappalyzer is a technology profiler that shows you what websites are built with).
I discovered that example.com used Symfony web framework.
Now open dirsearch and scan your website example.com.
I have found an interesting file which is “app_dev.php”.
Note: Dirsearch is an advanced tool, it allows hackers to perform a complex web directories discovery, with a customized wordlist, impressive performance, speed, high accuracy, advanced correction, and modern brute-force techniques with relevant outputs.

HttpKernel Component: The Symfony kernel has a request profiler component (Symfony\Component\HttpKernel\Profiler) that gathers information about resquests and responses, and associate them with a token. The web profiler bundle, as its name implies, provides a web interface to access this data, under the _profiler/{token} path.
Let’s check this url on the browser https://example.com/app_dev.php/_profiler/ and I found debug mode is enabled and got a profiler token to access Symfony Profiler.

Now click configuration menu and I got the phpinfo file or if you open this url you will get phpinfo page.
https://example.com/app_dev.php/_profiler/phpinfo


I knew Symfony Debug toolbars allowed reading files that could expose sensitive information.
Open files in PHPStorm from you Symfony application: (Learn about PHPStrom)
If you want to open files in PHPStorm directly from the Symfony debug toolbar there is a neat trick you can use. This is very helpful when you quickly want to find a controller or when you got an exception.
// /config/packages/framework.yml
framework:
ide: “phpstorm://open?file=%%f&line=%%l”
Now visit this url https://example.com/app_dev.php/_profiler/open?file=
You will see, The file is not readable.

We know that the Symfony web framework has a database default configuration file location, which is app/config/parameters.yml
Now open this link https://example.com/app_dev.php/_profiler/open?file=app/config/parameters.yml

Wow Boom!
I have found database, mail server credentials, some api keys and etc.

If you want you can check this files for sensitive informations after /open?file= file location.
src/Kernel.php
public/index.php
config/bundles.php
config/routes.yaml
config/services.yaml
/_profiler/phpinfo
Mitigation:
Disable the debug mode by setting APP_DEBUG to false. Debug mode should be disabled in the production environment.
You can watch this video:
